Introduction
report begins with a review of the literature on use GPS (Global Positioning System) technology. The engineering physics literature suggests development and application of RFID (Radio Frequency Identification) technologies.purpose of the report is to determine the most effective scope of RFID technology for printing companies in Russia, as well as indicate the prospects for their further development.work is divided into three parts. In the first part, it is said about Radio Frequency Identification System. In the second part, it is said about advantage of software for RFID. In the third part, it is said about application RFID - system.this project, in an attempt to explain a wide range of applications the RFID technologies county archives were consulted. These proved a valuable resource.extensive body of literature exists on the RFID technology that is used to describe a system that transmits the identity of an object or person in the form of a unique serial number, using radio waves. The present study draws primarily on the works of Samet Akpinar and Hakan Kaptan.
1.
Radio Frequency Identification
term "Radio Frequency Identification" is a method of identifying a physical object, in compliance with which is supplied RFID tag (tag, smart-label) microprocessor unit for receiving, storing and transmitting identification data with the radio interface. The radio frequency identification (RFID), infrared sensors, global positioning systems, laser scanners and other information sensing device, according to the agreed protocol, to any article connected to the Internet up to information exchange and communication, in order to achieve intelligent identify, locate, track, monitor and manage a network. Internet of Things concept is put forward in 1999. Internet of Things is the "material objects connected to the Internet". This has two meanings: first, the core of networking and infrastructure continues to be the Internet, is in the Internet on the basis of the extension and expansion of the network; second, the user-end extended and expanded to any article and articles, information exchange and communication. RFID is a technology with important business value and huge potential. RFID promises to replace the old barcode and contributes to the real time visibility of the goods, regardless of the location of the supply chain. We find RFID applications in various fields, but its main use is in tracking objects (C. Sun, 2012, p.1).
Types of RFID - tag
its simplest form, RFID is a concept similar to barcode technology, but without requiring a direct visibility of the monitored entities. Just like bar code systems require a proper optical reader and special tags applied on products, RFID needs a reader equipment and special tags or cards attached to the products in order for the products to be tracked (C. Sun, 2012, p. 2)power supply:transponders have their own power source, so that they can transmit data at a fairly long distance. Active transponders are used, among other things, the electronic customs information systems.transponders have no own power source and receive energy from the electromagnetic field of the reader. Passive transponders are used, for example, code cards in warehouse logistics.passive RFID-tags, also called semi-active, very similar to passive tags, but are equipped with a battery that provides chip Power On. Thus the range of these markers depends on the sensitivity of the receiver of the reader, they can function at greater distances and with better performance.types of memory:
"RO" (Read Only) data is written only once, just in manufacturing. Such tags are useful for identification only. Any new information in them can not be recorded, and it is virtually impossible to forge.
"WORM (Write Once Read Many) except the unique identifier tags contains such a write-once memory unit, which can then be read repeatedly.
"RW" (Read and Write) such tags contain an identifier and a memory unit to read / write data. The data therein may be overwritten by a large number of times.execution:adhesive paper or mylar tags; Standard plastic cards; Disk labels; Different kinds of trinkets; Special version for harsh environments.the moment there is a huge variety of labels, so you can pick the right performance for every task, depending on the needs of the customer.
The overall architecture of RFID-systems
RFID system mainly consists of two parts: the Reader and the RFID Tag, between them through radio frequency way to communication. Each tag has a unique electronic code, be attached to each object to identify the different objects, and some labels can also store related objects of simple information. Reader will launch to label read signals, and receive tag Morris information, then carries on the preliminary treatment of information and send back backend systems. A typical RFID system structure is shown in Figure 1.
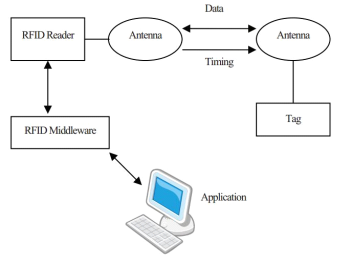
Fig. 1. RFID system structure
working principle of RFID is: the reader sends out radio waves of specific frequency energy to the electronic tags, electronic tag receives the radio waves. If is a passive tag, the induced current obtained with the energy stored in the chip information sent to the reader, if is an active tags, the active information in the chip of a particular frequency of the signal sent to the reader. Reader receives the feedback signal sent to the information system for processing.with other identification technology, RFID identification system have more advantages, such as no-contact, high degree of automation, durable and reliable, recognition speed, adapt the working environment, enabling both high speed and multi-tag identification and so on. Meanwhile, it does not need artificial view that manufactures barcode which saves Labour costs, and solved the two difficult problems in retail: out of stock and loss of goods (due to theft and supply chain to be disturbed for the loss of product) (Z. Mingxiu, 2012, p. 3).
Reader
Mandatory element of the RFID system is the reader that provides access to information stored on the transponder. The reader generates an electromagnetic field that activates the transponder. It, in turn, transmits the coded information reader. Depending on the bandwidth and the type of transponder data can be read at distances from a few centimeters to several meters. Are stationary and mobile.
RFID standards
Standard ISO 15693 (13.56 MHz) standard ISO 18000 (860 MHz) common technology, characterized by difficulties counterfeit labels. Best examples of tags can operate at a distance of 1 meter. The most promising technology, wherein increased reading speed, as well as a range of from 1 to 7 meters without line of sight.
RFID Security Threats
security threats to RFID technology can be put into several classes; Sniffing (or Eavesdropping), Spoofing, Cloning, Replay, Relay, and Denial of service attacks. The highest levels of security risks to an RFID network are sniffing and eavesdropping attacks. Eavesdropping/sniffing is an unauthorized access to tags. A rogue reader can read a tag and record information that may be sensitive and confidential. Spoofing attacks involve secretly scanning as well. It is not only recording a data transmission from a legitimate tag but also copying the original tag’s ID and making itself appear to be valid. Replay attack involves using a tag’s response to a rogue reader’s challenge to impersonate the tag. Relay attacks are alike to the replay attack but it delays the valid tag to response to the authentic reader. The last type of threat is the denial of service attack. It is against the accessibility of the RFID system and can hit any portion of the system (tag, reader, and controller-backend computers), such as removing the RFID tag from merchandise before it is checked out of the store, and swapping and placing tags on merchandise that has a lower cost. All attacks affect database integrity on the backend systems because of the inventory mismatches. (L. Burton, 2013, p. 3)
Software
component integration with the accounting system of the developers involved in decisions (Solution Providers), such as Taxonomy. Professionally built system does not require retraining of personnel, not force transfer / convert data without disrupting the normal rhythm of the enterprise. All the advantages of contactless identification technology will be available in a familiar programming environment. radio frequency identification tagcompany has already implemented RFID integration with the most popular accounting programs and business management, such as Microsoft Navision / Axapta, belonging to the family 1C (1C-Addressable warehouse, warehouse-VIP 1C, 1C-Enterprise), library information systems IRBIS, Ruslan, Mark SQL.
Application
libraries have implemented RFID systems in their book exchange. Scope of RFID-technology is virtually unlimited.of borrowing and returning back of the books are done simply by using RFID tags. Thus using the automation, information about library usage could be kept under record (S. Akpinar, 2010, p. 5)product values in cultural institutions (museums, visitors can using a personal digital assistant PDA (Personal Digital Assistant) to request information about the exhibits, which exhibits supplied transponders RFID. This museum staff receive information about what exhibits are often particularly interested in). Visitors to the store, leaving the trading floor with a basket of purchases will receive an invoice after crossing zone scanning device that reads information from all smart labels objects lying in the basket. Hospitals in the U.S. and in Germany also use radio frequency identification to facilitate the identification of patients and optimize their placement in the wards. Patients are provided with handmade bracelet with integrated transponders in them, which are coded patient name and number of his medical history, stored in an electronic database.Canada, from September this year, farmers were branding cattle by placing transponders on the animal's ear. Thus, when a sudden outbreak or epidemic herd becomes possible to quickly isolate.Russia in recent years has been a steady interest in radio frequency technology. Suppliers are increasingly getting requests from companies on the cost of implementation, as applicable to the project requirements are becoming more reasonable and specific. According to experts, the peak demand for RFID, still ahead. RFID-tags is forecast promises to be the most popular and media technology in the world, capable of competing on the spread of mobile phones.prospects and directions of development. In the area of food products technology can improve safety in food consumption because of low quality products can be returned to the manufacturer. Tags control the amount of autopsies packaging. Tags control the amount of temperature differences and their significance. RFID labels will appear on the "roll" band, showing information about the product or the user himself can control the speed of scrolling of the text using slider Sound RFID-labels.
Conclusion
is a non-contact automatic identification technology, it is through radio frequency signal automatically identify target signal and access to relevant information, and the backup support for the information processing software and applications of the technology. Meanwhile, RFID is future information storage extraction and processing of mainstream technology, more and more international companies have joined this technology development research, In recent years have shown that large-scale development of the situation, RFID concern by the market extent as any kind of emerging technologies. In e-commerce logistics relying on the tripartite, RFID is the key technology in informationization, the logistic informationization is logistics automation premise, logistics automation can enlarge the logistics operation capacity, and improve labour productivity to reduce logistics operations mistakes. RFID in logistics automation can be seen in the three prospects are extremely optimistic.
References
1. S. Akpinar, H. Kaptan. [2010]. Computer aided school administration system using RFID technology. ELSEVIER journal. <https://ac.els-cdn.com/S1877042810007391/1-s2.0-S1877042810007391 main.pdf?_tid=b7a42b20-f2cb-11e3-80f2-00000aab0f01&acdnat=1402644432_d8a97130ed8068a041c1916698469d25>. Accessed October 6, 2014.
. C. Sun. [2012]. Application of RFID Technology for Logistics on Internet of Things https://ac.els-cdn.com/S2212671612000200/1-s2.0-S2212671612000200-main.pdf?_tid=d514efe6-f2cb-11e3-bbed-00000aab0f27&acdnat=1402644481_7784cb1f7d0cc55bd199091132f41770. Accessed October 6, 2014.
. https://ac.els-cdn.com/S187538921200764X/1-s2.0-S187538921200764X-main.pdf?_tid=f2918d9a-f2cb-11e3-be66-00000aacb362&acdnat=1402644531_f747cdaa464b775d2da05bfac20cf599. Accessed October 6, 2014.
. https://ac.els-cdn.com/S2212671613000437/1-s2.0-S2212671613000437-main.pdf?_tid=206f8d34-f2cc-11e3-8d69-00000aab0f6b&acdnat=1402644608_6e10dd7e57fbd1d54a81a83045556435. Accessed October 6, 2014.
. https://ac.els-cdn.com/S1026309812000727/1-s2.0-S1026309812000727-main.pdf?_tid=c1c96a24-f2cc-11e3-bc3c-00000aab0f27&acdnat=1402644879_5e2faf1449f599e8e63671ca1bcca6e4. Accessed October 6, 2014.